Virtual CISO (vCISO)
So how does an organization that either does not have or is cutting back on security budgets make sure that it has executive leadership that is focused on information security? One way is to hire a virtual CISO (vCISO), also known as an on-demand CISO.
InDX
Technivorus Digital Transformation platform where organizations leverage the latest technologies to propel their business.
Strong Presales & Solutioning:
Our expert solution architects build innovative and effective solution stacks and post a detailed analysis of the situation which includes and is not limited to network topology, security, and physical infrastructure audits.
In-house expertise:
Technivorus has created robust capabilities through investments in emerging technology products & solutions.
360-degree customer support:
A dedicated team of L2 & L3 certified engineers to provide diagnostic, telephonic, and on-site support. We also offer a 4-hr CTR (Call for Resolution).
A Virtual Chief Information Security Officer or vCISO is a service designed to provide outsourced executive-level specialist cyber and information security expertise to organizations on a part-time basis.
A vCISO service is tailored to your organization’s specific cyber and information security maturity, capability, and needs. It can be a combination of on-site and remote access to your own virtual CISO who can provide executive-level advice and steer your cyber and information security strategy.
The vCISO service can range from a few hours per month to a fully outsourced information security function. The services can also be scaled up or down to adjust to your according to your changing information security requirements and maturity over time.
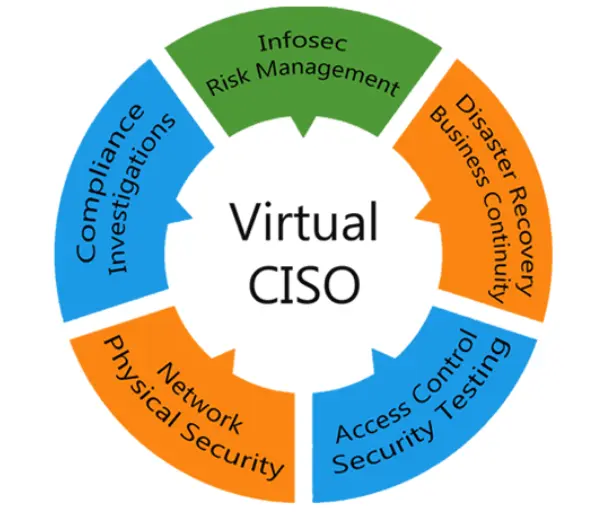
Technivorus vCISO Advisory Services are drawn on the experience of former CISOs from a variety of industries—from professional services firms to multinational conglomerates—and bring a valuable blend of technical, executive, and organizational experience. They are among the most accomplished technical experts practicing today, with special insight into evolving threats and solutions from their work at the front lines of cyber security. Technivorus vCISOs are supported by our global, multidisciplinary team that includes former information technology and security executives; digital forensic scientists; intelligence analysts; and regulatory specialists from a wide variety of industries. This high-caliber team will help put your entire information security program on the maturity fast track.
Finding an experienced, well-qualified CISO in today’s competitive information security job market can be challenging, time-consuming, and expensive. If you need a CISO now, then this is the perfect time to consider Technivorus Virtual CISO Advisory Services.
Why Hire a vCISO?
Expertise Across Industries
vCISO works with various clients in unique industries, exposing them to opportunities not available to CISOs working in isolated verticals. The security knowledge gained by a vCISO from each unique client environment ensures continual growth and improved expertise for the security leader, which positively impacts each client the vCISO leads.
Flexibility in Unique Business Environments
Virtual CISOs are prepared to begin working immediately with little onboarding time and can adapt to almost any setting. By their very nature, vCISO can enter a new environment and quickly adjust as business and security demands require. vCISO first gain a thorough understanding of each organization’s business model, company culture, risk tolerance, and objectives. From there, they gain an understanding of security risks faced by the organization. With a full view of the security landscape, the vCISO will communicate the findings to help clients make the appropriate security decisions for their environment.
The efficiency with Core Competencies
A virtual CISO fills in the security gaps where organizations need it most. By focusing on cybersecurity strategy and implementation, vCISO relieves internal teams of the daunting responsibility. This enables both internal staff and cybersecurity professionals to remain dedicated to their respective core competencies.
Objective Independence
vCISOs are not swayed by internal politics or personal career goals. vCISOs are independent third parties with an objective viewpoint and goals of helping clients make the best security decisions for their business.
Economical
Technivorus vCISO programs generally cost a fraction of a full-time CISO and supporting security team. According to Silver Bull’s May 2016 report, the Median salary for a CISO is $223,000 per year. The base salary does not even include the expenses incurred with additional employee headcount. On average, Technivorus vCISO clients pay a fraction of what it would cost to hire an in-house CISO. vCISO clients also gain access to the expertise of an entire team, which eliminates the inherent skills gap of a single employee.
| vCISO | CISO | |
|---|---|---|
| Resources | Security Leader + Security Resources | Security Leader |
| No. of Resources | Team | Single |
| Roles | Strategic + Operational | Strategic |
| Scalability | Yes | No |
| Project Start | Immediate | 3-6 Months |
| Turnover | 0 | 1.5 Years |
| Team Integration | Full | Full |
| Value of Services | ***** | *** |
| Total Cost | $$ | $$$ |
Our Offerings
Technivorus’ virtual CISO Advisory services can give you the technical know-how and business perspective you need to make an immediate effect. Our professionals have worked in a range of industries providing the following services:
Network security
Technivorus' CISO as a Service delivers high-level network security advice and an in-depth examination of potential risk areas.
Data security
Our CISO services can handle data security concerns specific to your company, allowing your technical professionals to focus on areas where they excel. .
Infrastructure security
By discovering application vulnerabilities, misconfigured technologies, and insecure components, we assure the security of your system. We share a strategic and tactical experience as we discover vulnerabilities to help you improve your security posture.
System security
Our virtual CISO services function as a semi-permanent system security executive fixture within your firm focused on immediate and long-term objectives.
App security
We concentrate on safeguarding all-important applications that drive your business, looking for vulnerabilities and faults in your apps and practices, and always present a remediation plan to ensure that all issues are resolved.
Governance, Risk & Compliance
The vCISO managed services from Technivorus will keep your information security operations compliant with all regulatory standards.
Advanced Threat Protection
Technivorus' powerful analytic tools help counter advanced attacks by providing rapid visibility, evaluation, context, and response to harmful network traffic's contents and behaviour.
Why our vCISO?
Our vCISO service gives companies access to a pool of specialists and experienced cyber safety practitioners who take on the role of a Chief Information Security Officer in your business. Our affordable V-CISO provider brings ride-in management and skills to assist define, sketch, and execute a bespoke method unique to your organization.
Our V-CISOs are supported by using our compliance and governance group contributors to ensure we meet all the varying necessities of your business.
Technivorus team of experts includes seasoned former CISOs from a variety of industries who can strengthen your existing staff, set strategic objectives to support business-critical technology demands and balance IT administration, as well as establish clear communication with the board of directors, investors, and government agencies.
Whether you are looking for an interim CISO, a resource to support your CISO, or a longer-term arrangement, Technivorus Virtual CISO Advisory Services provide the leadership you need, when you need it.
You can rely on a vCISO from Technivorus to have the technical expertise, business acumen, and communication skills to make an immediate difference. Our experts have served in a broad range of industries for companies of various sizes and will know how to align information security strategies with your company’s unique needs and challenges.
Services and offerings include:
- Setting or directing privacy and security policies, standards, procedures, and guidelines
- Managing and directing information security teams
- Engaging with executive management
- Running risk assessments on operational security
- Providing threat intelligence and manage enterprise security
- Crisis management
How Do We Do It?
We apply industry standards, regulations, and best practices to objectively assess the risks to your information security assets. As a result, you have a thorough understanding of where you are most vulnerable and a plan to manage the risk. Simply stated:
We assess existing information security programs (administrative, physical, and technical security controls) and We develop, implement, and manage information security programs tailored to each client’s specific security needs.
Proactive Security
(Prepare & Detect)
- Organization & Awareness
- Risk Management
- Security Policy
- Asset Management
- Vulnerability Assessment & Penetration Testing
- Asset Protection
Reactive Security
(Respond & Restore)
- Identity & Access Management
- Security Monitoring
- Incident Response
- Operations Efficiency
- Board Reporting
Technivorus Virtual CISO Advisory Services Help You Prepare, Protect and Strengthen Defences
Our vCISO Advisory Services are tailored to your specific situation and information security needs. While you have several options when it comes to the scope and length of services, there are four areas where most organizations benefit from the experience of a vCISO:
Strategy Definition: Guiding executives across business function and IT, Technivorus vCISO helps identify business threats, provides a baseline for your current security program, and defines security strategy in line with business objectives and technology strategies.
Our phased approach helps ensure an effective and efficient strategy that leverages NIST 800-53 and can be mapped to multiple cyber regulations (e.g., PCI, HIPAA, GDPR, FINRA, NYDFS).
Assessment: Evaluating culture, processes, and technologies from a security governance perspective, Technivorus vCISO develops prioritized actions to help effectively manage your information security strategy and program. Assessments can include:
- Interviews with stakeholders across the technical, business, and executive teams as well as gathering documentation
- Robust reviews of a variety of areas, including information asset management, acceptable use policies, data classification, threat and vulnerability management, and third-party management
Oversight: Based on the assessment findings, Technivorus vCISO can provide various types and levels of ongoing support, including:
- Developing policies and procedures to close gaps in documentation
- Developing a remediation plan with actionable, prioritized recommendations
- Implementing the remediation plan
- Providing ongoing strategic guidance that is less intensive, but assists the organization in maintaining long-term goals
Training: Security awareness is an important part of maintaining a robust program. Your vCISO can recommend and help implement training on topics for every level of user group within your organization. This can range from the highly technical (e.g., secure coding practices) to general data handling education to combating business email compromise. The vCISO can also oversee controlled phishing campaigns, conducted by Technivorus, to determine security awareness levels among employees.
IT Environment Security Design: For organizations looking to build from the ground up, Technivorus vCISO can provide your team with necessary system hardening configuration guides and network designs. This will also include multiple security protections and incident monitoring controls.
Virtual CISO Services and Responsibilities
Like a standard CISO, the vCISO services and offerings are remarkably similar. However, what a vCISO will be responsible for will vary and depend on the specific needs of the organization. Generally, some of a vCISO’s responsibilities will include, but are not limited to the following:
- Providing the vision, strategy, direction, and implementation of the information security and compliance governance program
- Convey security goals to the organization’s board of directors
- Determining the proper security framework(s) with which the company must comply
- Understanding industry trends and leading the team in architecting security solutions
- Help define security budgets and most appropriate and cost-effective security solutions
- Providing guidance and support in achieving compliance requirements the company may have
- Managing the Information Security team
- Defining, Planning, writing, reviewing, and approving policies, procedures, standards, and processes
- Supporting or leading the Incident Response team
- Defining the acceptable level of risk and managing the organization’s risk
- Review current internal security controls
- Guide the annual security planning and training
| Define | Manage | Optimize |
|---|---|---|
| Policies & Standards | Review & Update | Operationalize Governance |
| Tech Security Controls | Expand Control Set | Regular Control Audits |
| Develop Risk Register | Appy Threat & Impacts | Risk Reporting |
| Define Scope of Vendors | Foster Vendor Remediation | Contractual Risk |
| Define Remediation Timelines | Fulfill Remediation Times | Report Remediation Metrics |
| Establish Exception Guidelines | Ensure Proper Cadence | Reduce Exceptions |
| General Security Awareness | Apply Targeted | Enterprise Modular Training |
| Understand Compliance Landscape | Training | Audit Scope Reduction |
| Operationalize Compliance |
Compliance Assurance / Project Management Methodology
Before the kickstart of the engagement
- Clearly defined goals and objectives
- Critical Success Factors Identified
- Key Risk Areas Identified
- Roles & Responsibilities Defined
- Deliverables agreed upon
- Change management Process defined
During the engagement
- Regular progress updates through agreed-upon channels viz. email or in the form of reports
- Expectations Management
- Any change to be managed as per defined Change Management Process
- Dashboard based reports for Executive management and Technical / Implementation Teams with recommendations
After the engagement
- Project Sign of
- Project final report with all the findings and recommendations
- Roadmap for next steps
- Continual Improvement has proven through matrices and Dashboards
FAQ'S
The vCISO team is responsible for structuring policies and procedures to align with company culture, risk tolerance, and compliance requirements. A tailored approach is integral in the creation of an effective security program. Most vCISO engagements begin with an IT risk assessment, which identifies areas of needed improvement and helps set priorities for the security program. Once deficiencies are identified, a remediation plan is generated to begin addressing security gaps. After remediation is complete, we reassess, help present the findings to executive leadership, and repeat the steps.
The demand for vCISO services has grown rapidly over the past few years. As information security threats increase and businesses remain the primary target, the demand for security professionals will continue to rise. The employment gap between the demand for security professionals and its supply is widening. This drives a competitive market for security professionals and places a major burden on companies seeking to staff for their cybersecurity needs.
This is where a vCISO offers its value. Virtual CISO services provide organizations that would otherwise not be able to hire a qualified security candidate the ability to work with an experienced CISO and security team, without increasing their organization’s headcount. Many organizations do not need a full-time CISO, they need an independent security professional to lead their organization by assessing cybersecurity issues, building a cybersecurity program, and ensuring the achievement of proper security milestones.
There are organizations of all sizes in various industries that are benefiting from vCISO services. For example, at Technivorus we work with businesses in healthcare, manufacturing, technology, analytics, printing, marketing, insurance, retail, and finance. Regardless of the industry, technology plays a major role in operating a business, and with technology comes security risk.
Each business is unique, and every organization handles risk differently. However, the approach is the same with every organization. First, a vCISO helps an organization understand its risk, and second, the vCISO helps organizations make the appropriate security decisions to align with business objectives.
Companies without an internal, dedicated cybersecurity leader should hire a virtual chief information officer. Virtual CISO advisory services are crucial for assisting in thinking strategically about information security practices, policies, and procedures and providing a realistic blueprint to stay protected.
Your virtual CISO team will get to know your company inside and out, dig into your present information security rules, and develop solutions specific to your needs. The fact that your virtual CISO team will be ready at a moment’s notice in the case of a threat or breach detection makes virtual CISO advisory services so effective.
